We are a company that specialises in cyber security.
 From secure architecture design to full on penetration testing, binary dissassembly, code review, security training and consultancy, we are here to cover all your needs.
From secure architecture design to full on penetration testing, binary dissassembly, code review, security training and consultancy, we are here to cover all your needs.
Our consultants are well known in the security industry for their research and have an enthusiastic approach to cyber security. We provide services at a higher quality and lower price than our mainstream competitors.
Services
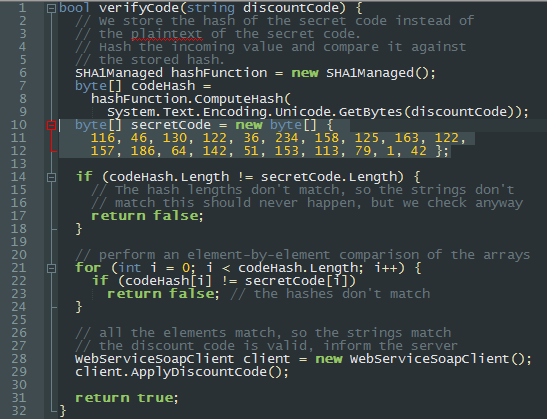 Security Code Review
Security Code Review
Get an experienced pair of eyes to review your code for security flaws. We can handle any language you throw at us: from close-to-metal C to top-of-stack Ruby. Any code provided is kept fully encrypted and deleted after the engagement. Our NDA are honoured in perpetuity.
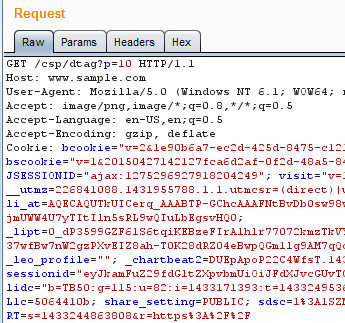 Penetration Testing
Penetration Testing
Hands on manual penetration testing of web applications, infrastructure, networks, hardware, embedded devices and thick clients. We attempt to attack your systems like a real hacker would, and delivery a report detailing what we achieved, and how it the flaws found can be fixed.
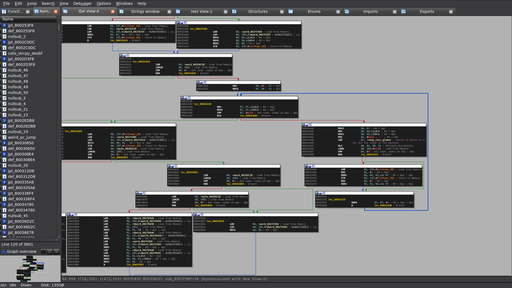 Reverse Engineering
Reverse Engineering
No code? No problem. Our consultants have decades of experience reverse engineering software and hardware for interoperation, algorithm identification and vulnerability research in x86, x64, ARM, MIPS, SH-4, C#, Java, Rust, Go and others.
 Secure Architecture
Secure Architecture
Did you know that it costs 1000 times more to secure a product after release than in its development phase? Our consultants can help you plan and develop your product to avoid costly security mistakes. Even if your product has already been released, we can still help you uncover hidden risks with our Threat Modelling framework.
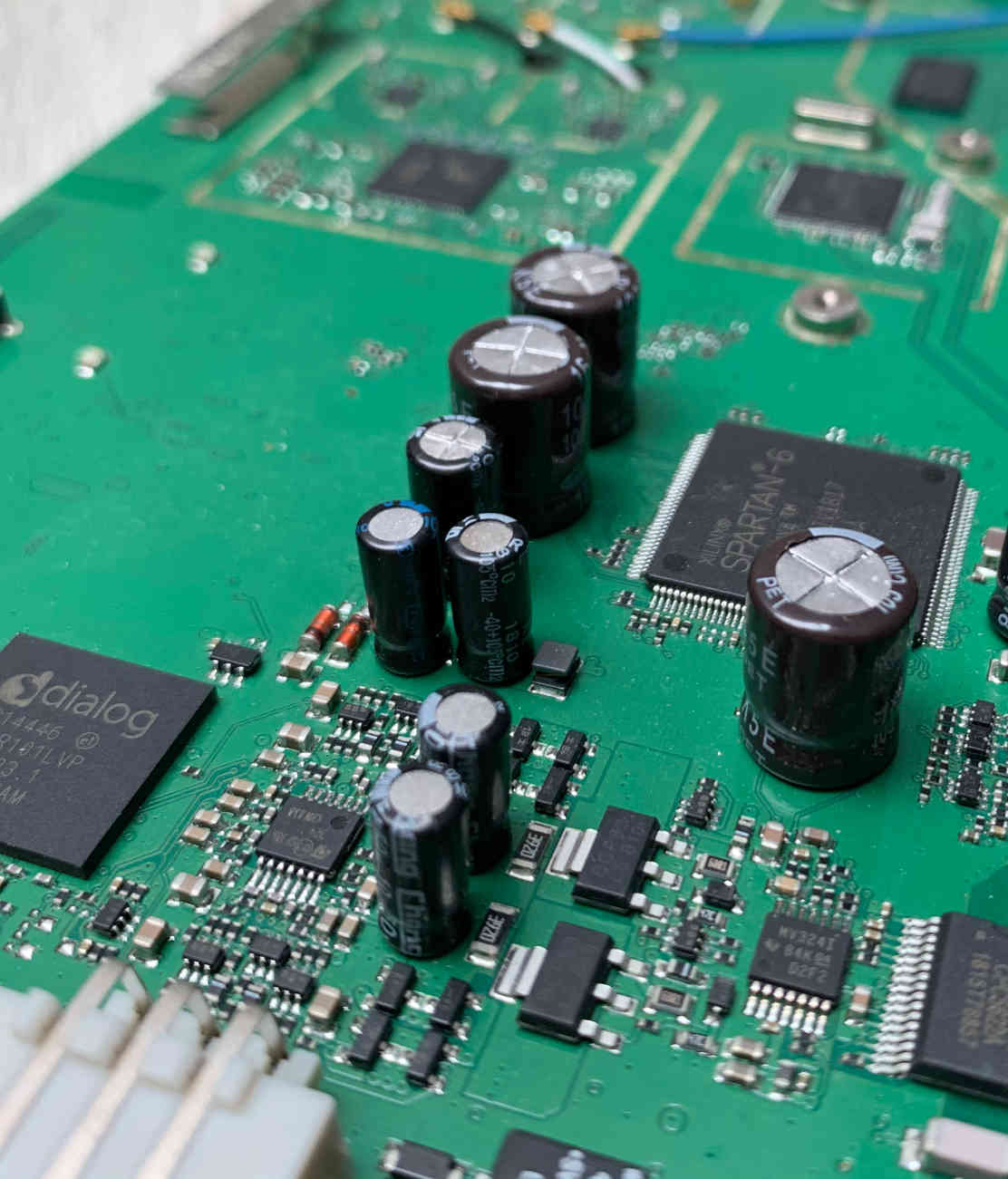 Product Security
Product Security
Leveraging our consultants' experience in Penetration Testing, Code Review, Reverse Engineering, Hardware Security and many others, we regularly assist large and small organisations with securing their products. Our holistic Product Security service combines all this world class experience to help secure your products and their secrets.
 Incident Response
Incident Response
Have you been hacked? If so, we can help. We will immediately start investigating any suspicious activity in your network, determine how the intruders got in, throw them out of your network and help you plug the holes to avoid future intrusions. We also leverage our expertise to improve your Network Monitoring, logging and SIEM capabilities.